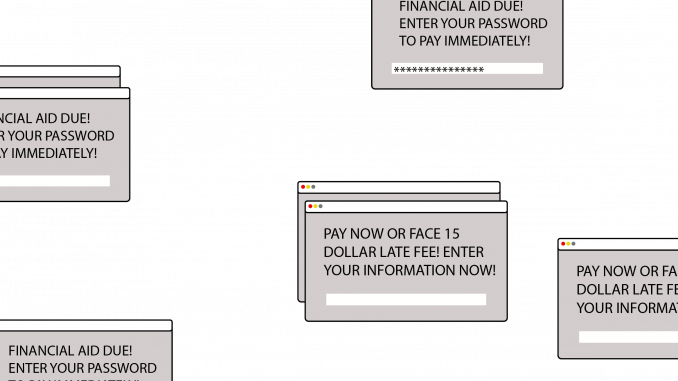
Temple University students are being targeted by an email phishing scheme that goes after financial aid refunds.
No one has reported having their financial aid refunds stolen, said Larry Brandolph, the associate vice president of Computer Services and chief information security officer.
Still, several students said they’ve received phishing attempts to their Temple email accounts.
The Department of Education warned higher education institutions in August that it identified the malicious phishing scheme, which targets students’ financial aid through fraudulent emails and accessing student portals.
Schools that do not require students to have two-factor or multi-factor authentication to access student portals, like TUportal, are more vulnerable to the attacks, Federal Student Aid wrote in a statement in August. The phishing campaign gains access to students’ financial aid refunds that the university returns through direct deposit.
While Temple uses this process to return refunds, the university does not require two-factor or multi-factor authentication on TUportal. Only faculty, staff and student workers, have access to this method for identity verification.
Brandolph said university workers have had access to multi-factor authentication on their TUportals since 2016. The university is working on building and implementing a multi-factor authentication method for the general student body within the next six months, he said.
MULTI-FACTOR VERIFICATION
The university is already licensed to provide two-step authentication to most students, faculty and staff, but has not yet implemented the technology for students who are not employed by the university, Cindy Leavitt, chief information officer and vice president for Computer Services, wrote in an email to The Temple News.
“We have deployed two-step for employee payroll services like direct deposit, benefit information and W-2s, which already is being used by student workers,” Leavitt wrote. “We are working on how to extend two-factor authentication for other student services in the next few months.”
Employees, including student workers, have access to staff tools in the Self-Service Banner, which includes multi-factor authentication, Brandolph said. Students who are not employed by the university do not have the same access, but often receive financial aid refunds through direct deposit on TUportal.
According to the most recent university factbook, more than half of full-time undergraduates received need-based financial aid during the 2016-17 academic year. Nationally, more than 19 million public university students receive direct federal loans, the DOE reported.
Brandolph said the phishing scheme is attempted on a daily basis.
“It’s a constant phishing scam, phone scams, we see it all, every single day of the week,” Brandolph said.
Freshman early childhood education major Anna Goodwin said she received several emails during the summer about financial aid offers and loans that she knew at the time were scams. Most of them, she said, made unrealistic offers.
“I could always tell when they were scam emails because they asked me to click on links or sign up for something,” Goodwin said. “My guideline for telling if they were fake was to decide if they were too good to be true.”
The DOE suggests colleges and universities report successful attacks to the federal government, but it is not required. The university does not report the scheme’s attempts, or keep record of the number of false emails sent to students, Brandolph said.
The FBI is also aware of the phishing scheme, Leavitt wrote, and has been providing educational resources to IREs about the attacks.
“The FBI will do some investigation at the local office levels, but phishing is a major focus for them currently,” she wrote.
HOW IT WORKS
The phishing campaign attempts to gain access to student portal accounts by sending a deceiving email, which prompts students to share account information, like their login to TUportal.
The emails appear to come from a university address and refer to enrollment and updates to direct deposit payment methods, according to the FSA. The attackers have done research and understand universities’ portal operations.
The scheme is successful because students provide the requested information and use just one method of authentication, a username and password. Attackers change the bank account information for financial aid direct deposit to their own bank accounts.

“The attackers are exploiting a common practice at many [higher education institutions]: the use of single-factor authentication to access institution systems,” according to the FSA.
There are other ways to receive financial aid refunds from the university, like through paper checks delivered by mail, but students can enroll in direct deposit for their refunds.
Freshman risk management and insurance major Lena Nguyen said her parents handle her tuition and financial aid, so she does not think the phishing scheme would directly affect her.
“I usually run everything by my parents because I don’t know anything about money,” Nguyen said. “I feel like it wouldn’t affect me that much because I’d be kind of careful about it.”
Parents of students are also vulnerable to attack, Brandolph said, because they often receive financial aid refunds through direct deposit on TUportal. Parents have not reported instances of being targeted by the scheme.
Senior psychology major Samantha Porter is a student worker in the Education Abroad Office. Porter’s mother, Debbie Porter, believes the two-step verification her daughter has access to should also be available to the general student body.
Debbie Porter uses direct deposit to receive her daughter’s federal financial aid refunds.
“Anyone who has a Temple email account should have that extra protection,” Debbie Porter said.
Samantha Porter said that while she has received several phishing emails and has access to the two-step authentication process, she has not set it up. She said since it is only a suggestion, not a requirement, she did not want to go through the process of creating it.
“I know there are instructions online, but I got really confused trying to read them, so I gave up,” Samantha Porter said.
Samantha Porter said most of the spam emails tried to get her to click on a link, and one was written as if it was from a professor. She deleted them immediately after receiving them, per the instructions sent to all Temple staff warning them about the emails.
She feared she could have been more vulnerable to these attacks because she does not have her two-step verification setup, Samantha Porter said.
PREVENTATIVE MEASURES
Many universities encourage students to use multi-factor authentication, while some even require it for all faculty and staff.
For example, the University of Maryland required all students to be enrolled in this method beginning Oct. 15, according to an email sent to students.
Penn State announced in September that the university mandates two-factor authentication for all its faculty and staff. It is also available to all students.
Information Technology Services sent an email to the Temple community on Sept. 26 with tips on how to spot phishing scams in emails. In effort to prevent the community from falling victim to email scams, ITS recommended that students and faculty search for clues in the body of suspicious emails to determine if they are false.

If the email is from an unrecognized sender, asks for passwords or personal information, has a tone of excitement, includes unexpected attachments or links and has writing and grammar mistakes, it could be from a cybercriminal, according to ITS.
The university also told students and faculty it will never ask for their personal information or passwords via email. Emails that ask for this information are likely a part of the phishing campaign.
ITS also has online resources that describe phishing schemes and how to identify them, including an example phishing email. The ITS webpage instructs students to forward suspicious emails to abuse@temple.edu and not to respond. The daily reported phishing attacks can be temporarily monitored on ITS’ System Status site.
Freshman accounting major Elena Van said she saw multiple suspicious emails in her inbox this summer. She said she does not know how to differentiate between real emails from the university and fake emails that could be part of a phishing scheme.
“I tend to be a really gullible person, so I don’t know how to differentiate whether or not [they’re] real or not, but I have received a lot of financial aid emails,” Van said.



Be the first to comment